![mac-applications-folder[4] mac-applications-folder[4]](http://cdn3.howtogeek.com/wp-content/uploads/2013/12/650x300xmac-applications-folder4.png.pagespeed.ic.s6vpvhZufG.jpg)
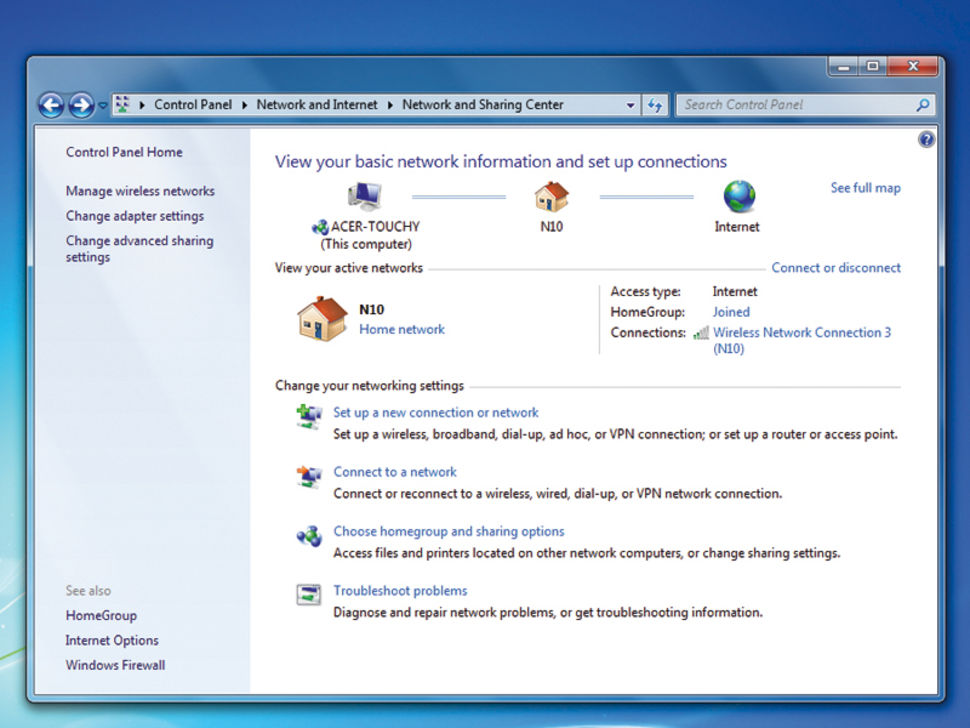
Installing software on a Mac is different from installing software
on Windows. There isn’t just one way to install applications on a Mac,
either — there are several different ways, depending on the application
you want to install.
New Mac users will likely find themselves asking a number of
questions: Why isn’t every application on the Mac App Store? What is a
DMG file, and why do I have to drag-and-drop the app’s icon after
opening it?